Update this article with a summary and a Q&A – the original text remains at the end for documentation purposes.
What happened?
Yesterday, Saturday, April 19th, several tenants worldwide experienced user blockages due to „User High Risk – User credentials leaked.“ The uncertainty among the administrators of these tenants was quite significant, especially since there was no communication from Microsoft for a long time. The best information was provided by a Reddit thread, which I summarize here.
Which tenants are affected?
According to the Reddit thread, there is no discernible pattern. Both large and small tenants are affected, including tenants managed by partners and those with direct payments to Microsoft. Tenants from all over the world, users with Business Basic up to users with E5, and tenants with and without Conditional Access are impacted.
How can I tell if my tenant is affected?
There are two indicators:
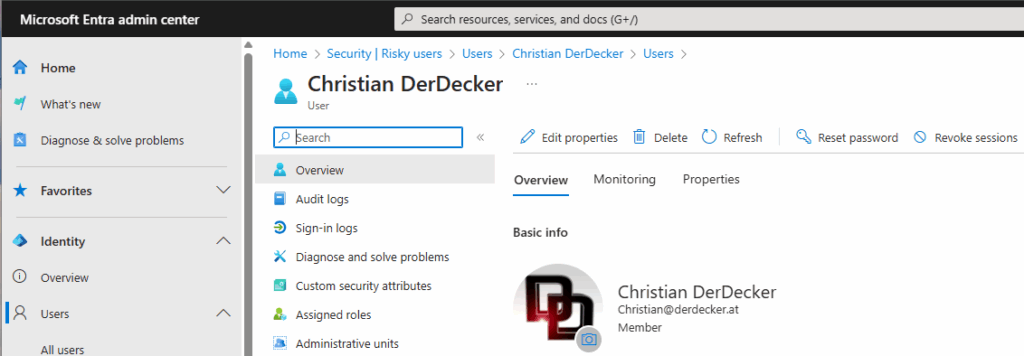
a) There are users with High Risk status who received this status on the morning of April 19, 2025, with the warning: „User credentials leaked“. This can be found at Microsoft Entra – Entra – Identity – Protection – Risky activities – Risky User.
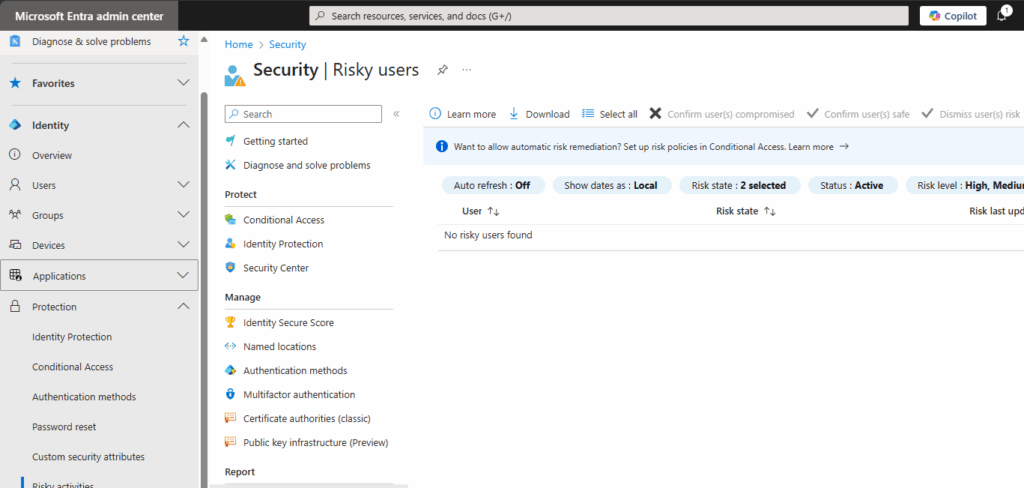
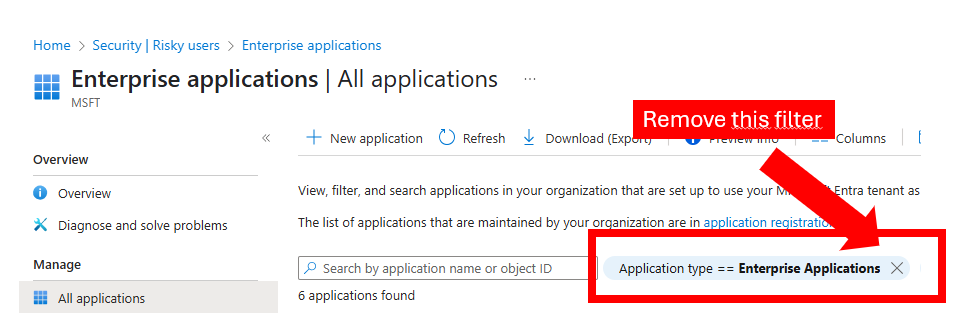
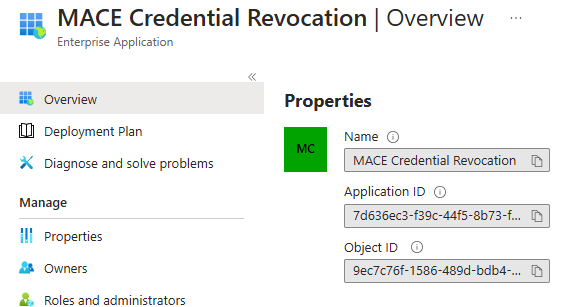
b) Microsoft has added an Enterprise Application called MACE Credential Revocation to the affected tenants. This can be found under Entra – Identity – Applications – Enterprise Applications. It is important to delete the filter „application type == Enterprise Applications“ before searching for the app.
How can I tell if my tenant is affected?
Several users got this evening (sunday) this answer from Microsoft to their support tickets:
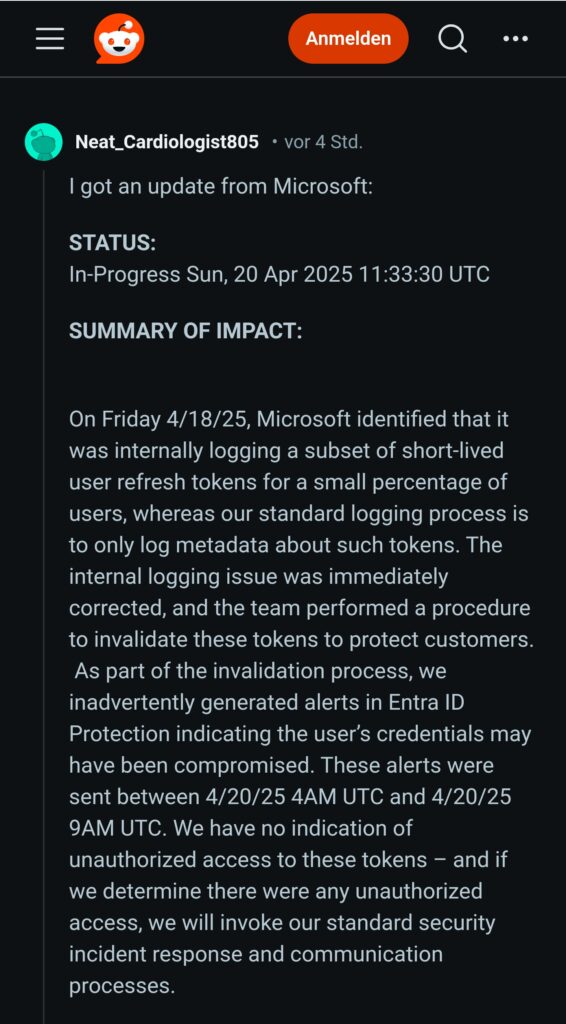
STATUS:
In-Progress Sun, 20 Apr 2025 11:33:30 UTC
SUMMARY OF IMPACT:
On Friday 4/18/25, Microsoft identified that it was internally logging a subset of short-lived user refresh tokens for a small percentage of users, whereas our standard logging process is to only log metadata about such tokens. The internal logging issue was immediately corrected, and the team performed a procedure to invalidate these tokens to protect customers. As part of the invalidation process, we inadvertently generated alerts in Entra ID Protection indicating the user’s credentials may have been compromised. These alerts were sent between 4/20/25 4AM UTC and 4/20/25 9AM UTC. We have no indication of unauthorized access to these tokens – and if we determine there were any unauthorized access, we will invoke our standard security incident response and communication processes.
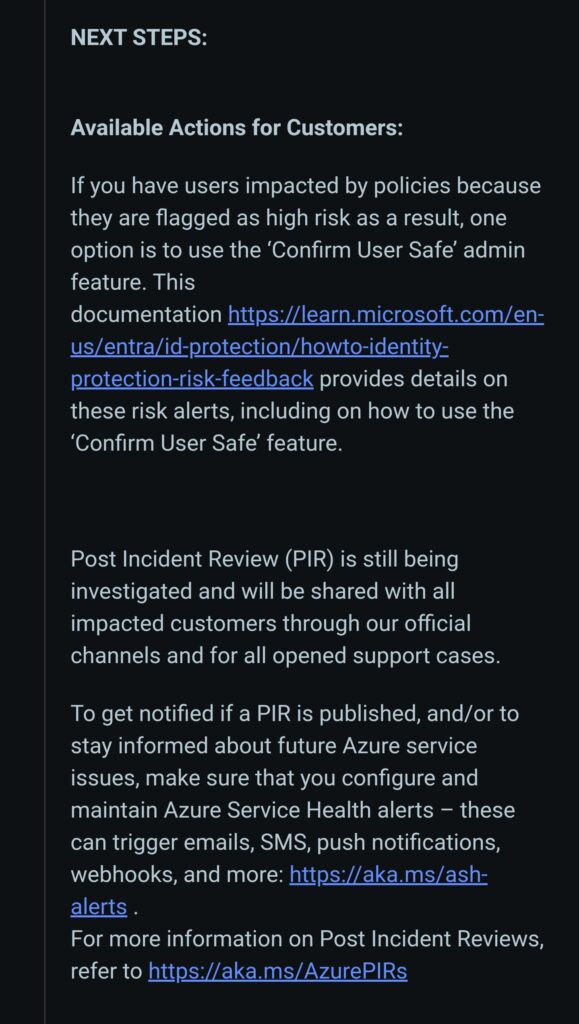
NEXT STEPS:
Available Actions for Customers:
If you have users impacted by policies because they are flagged as high risk as a result, one option is to use the ‘Confirm User Safe’ admin feature. This documentation https://learn.microsoft.com/en-us/entra/id-protection/howto-identity-protection-risk-feedback provides details on these risk alerts, including on how to use the ‘Confirm User Safe’ feature.
Post Incident Review (PIR) is still being investigated and will be shared with all impacted customers through our official channels and for all opened support cases.
To get notified if a PIR is published, and/or to stay informed about future Azure service issues, make sure that you configure and maintain Azure Service Health alerts – these can trigger emails, SMS, push notifications, webhooks, and more: https://aka.ms/ash-alerts .
For more information on Post Incident Reviews, refer to https://aka.ms/AzurePIRs
Stay informed about your Azure services
Set-up service health alerts to stay notified of future service issues, planned maintenance, or health advisories.Visit Azure Service Health to get your personalized view of possible impacted Azure resources, downloadable Issue Summaries and engineering updates.
How can I tell if my tenant is affected?
The affected users are blocked and cannot sign in.
The SAFE way to downgrade a user with High Risk is to change the user’s password and revoke all current sessions. The easiest way to do this is in ENTRA – Identity – Users – All Users – select the user – Revoke Session and Reset password.

(For safety, although it’s obvious: Sending the affected user their password via email is rather pointless, as the user cannot access their emails. Therefore, SMS is the better option here.)
If you are sure, that the User is only on High risk because of this action from Microsoft, you can flag the User as „Confirm user(s) safe“ in the risky users menue
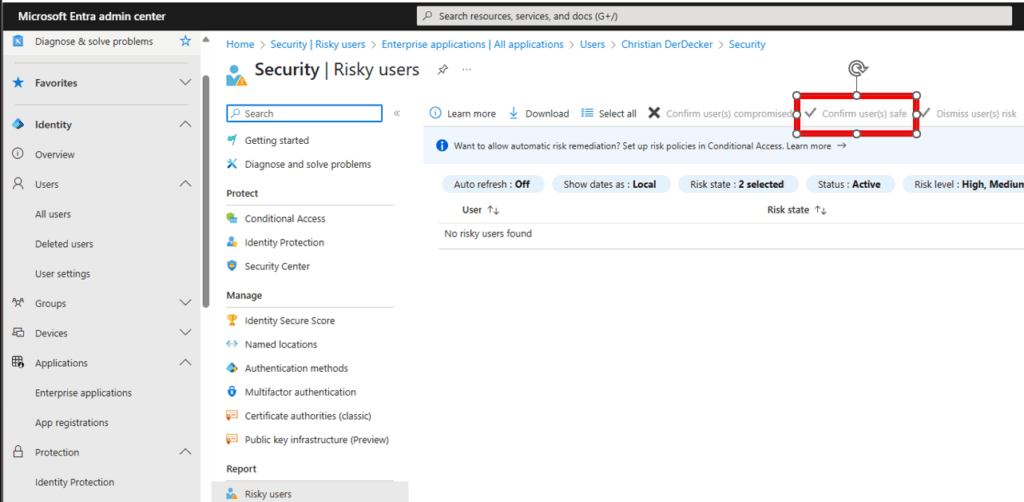
After a few minutes, the user disappears from this list and can sign in normally again.
Has there been any official communication from Microsoft about this?
Currently, I am not aware of any response – as soon as I hear something, I will update the blog article.
The contents of the first blog article remain here for historical reasons – the following texts were created on Saturday.
Since today, several tenants worldwide are experiencing cases where one or more users are being flagged as high risk. Cause: leaked credentials
Affected tenants can be identified by the presence of an enterprise application named MACE Credential Revocation.
There is currently no statement from Microsoft – there don’t seem to have been any attacks.
A password reset for the affected user clears the user risk.
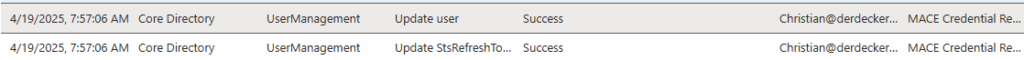
For my user it happened at 7:57 AM austrian time zone
I will update the post with new information as I learn more.
There is a redit discussion with a lot of information: https://www.reddit.com/r/sysadmin/s/0i3KuDWUVI
Following the Reddit thread, it becomes evident that there is no issue with phishing attacks or stolen PW files from other websites. This is because users affected include those who exclusively use Fido Keys and have long, complex passwords, as well as passwordless users who do not know their passwords at all.
From my perspective, this leaves only two possibilities:
a) it is a false positive (which I currently believe), or
b) an attacker had access to the password hashes in Entra (which we do not want to consider).
„A Reddit user received a somewhat useful response from support: Sounds valid to me… Let’s see…
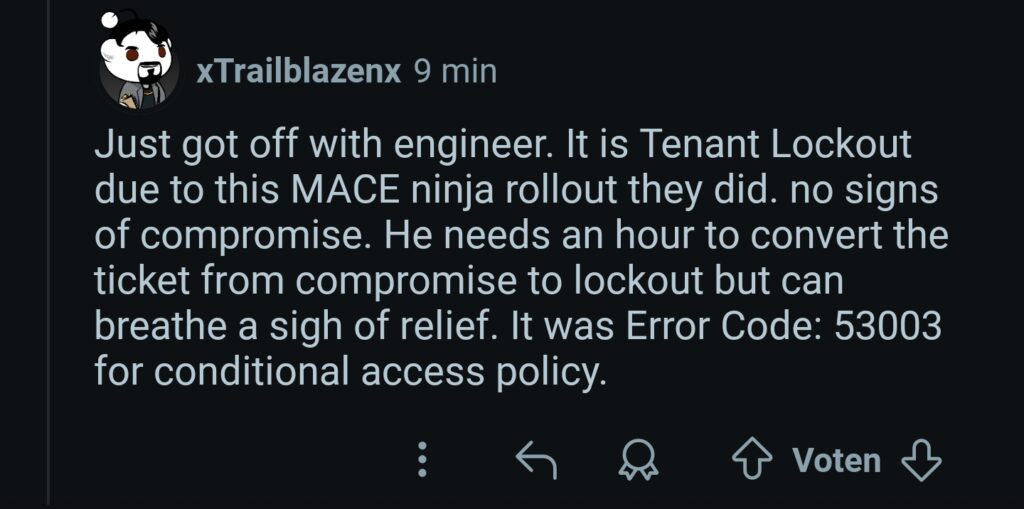
There is a new answer from Microsoft in one of the support cases:
What can/ should you do as an Entra Admin ?
Log into Entra
Open Security – Microsoft Entra admin center to see if and which users are affected
You find this menue item in Entra – Identiy – Protection – Risky activities – Risky users
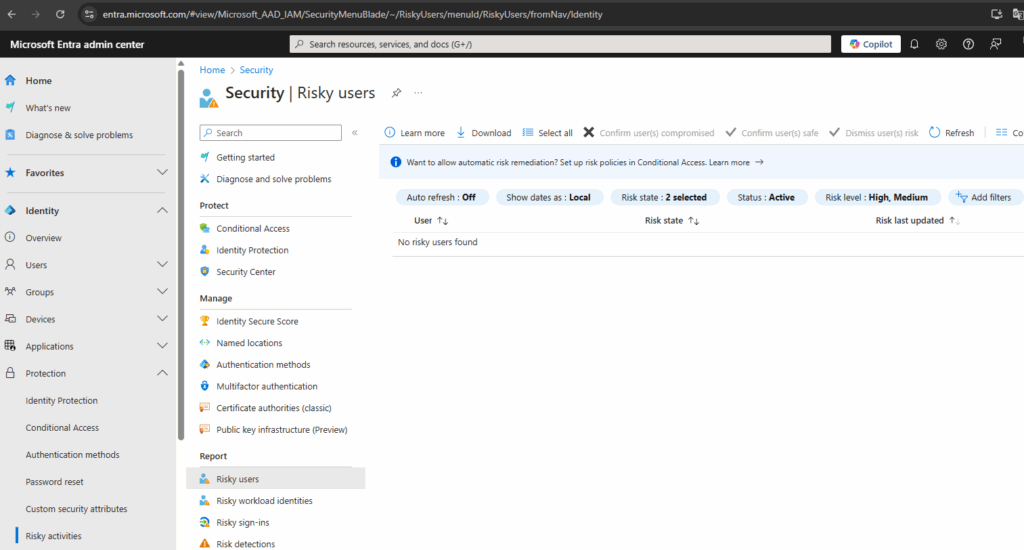
If you don’t check this report often, take a look at the „Risk last updated“ column – you might see users who were flagged as risky a while ago
One way to unlock the blocked users is to mark the user here and select „Confirm user(s) safe“ at the top – after a short time, the users can log in again. However, I can’t really recommend this method; the recommended way is definitely to change the user’s password!
So, go to the user in Entra ID, select „Revoke sessions“ to invalidate all authenticated sessions, and then use „Reset password“ to change the user’s password. For safety, a small tip (although it’s obvious): sending the user their new password via email is rather pointless – because they can’t access it. SMS is a good option here…